Culture Eats UX Strategy for Breakfast
The article summarizes 8 key programs that UX leaders employ in order to build and sustain strong UX cultures within their companies. These programs can be viewed as a “UX culture palette”. Each program in the palette is composed of activities which UX leaders can use to engage with the various stakeholders, teams, and business functions at their companies. The palette is a tool for thinking more broadly and systematically about practicing UX at scale within a business organization.
Culture Eats UX Strategy for Breakfast
The article summarizes 8 key programs that UX leaders employ in order to build and sustain strong UX cultures within their companies. These programs can be viewed as a “UX culture palette”. Each program in the palette is composed of activities which UX leaders can use to engage with the various stakeholders, teams, and business functions at their companies. The palette is a tool for thinking more broadly and systematically about practicing UX at scale within a business organization.
As companies and IT organizations are bombarded daily by an ever-growing number of cybersecurity threats and attacks, they struggle mightily to keep pace. The Respond Analyst solves this problem by automating deep analytical and probabalistic reasoning across massive security event feeds.
Operating at machine scale the Analyst is able to identify, correlate, and escalate security-related events in a fraction of the time required by human beings.
Security teams can now offload the boring, repetitive, mind-numbing tasks of security monitoring and triage to
a highly scalable, accurate, and effective decision engine.

Personas


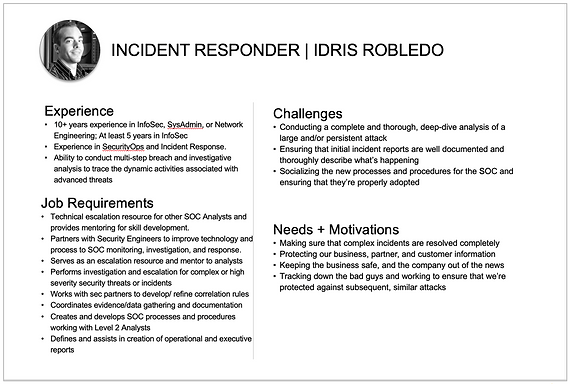
Journey Map
The end to end security operations journey. The green border rectangle indicates the use case for Respond Analyst.

Security Triage Journey: Large Enterprise
Large security operations have a wide degree of role specialization with tiered levels of responsibilities.
Event triage is usually assigned to the least experienced people, and eventually leads to job burnout.

Security Triage Journey: Mid-Size Company
Mid-sized companies typically have a few security people covering all security-related activities. Sometimes these folks have both IT and Security responsibilities. Security event triage often gets neglected due to general task overload.

Product
Just a couple of clicks to a powerful security incident report...

A dark themed experience for typical low-light security environments...

NOTE: Only showing limited product examples in this public venue
Recognition

Gartner names Respond Software as a 2018 Cool Vendor for Security Operations and Vulnerability Management

“It’s not often that I say, ‘Wow,’ but that is what I said when I learned about the Respond Analyst.”
Ed Amoroso
CEO, TAG Cyber
Global cybersecurity consultant
Thought-leader